This section provides an updated law enforcement view on the interlinked topics of the Internet of Things, Big Data and Cloud computing and services172.
The growing adoption of the IoT further contributes to the convergence of people, processes, data, and objects to deliver new or enhanced services such as precision personalised medicine173, and provide improved contextual awareness and decision support. This not only introduces cybersecurity risks and ethical questions but also creates a number of challenges in terms of identity, privacy and trust.
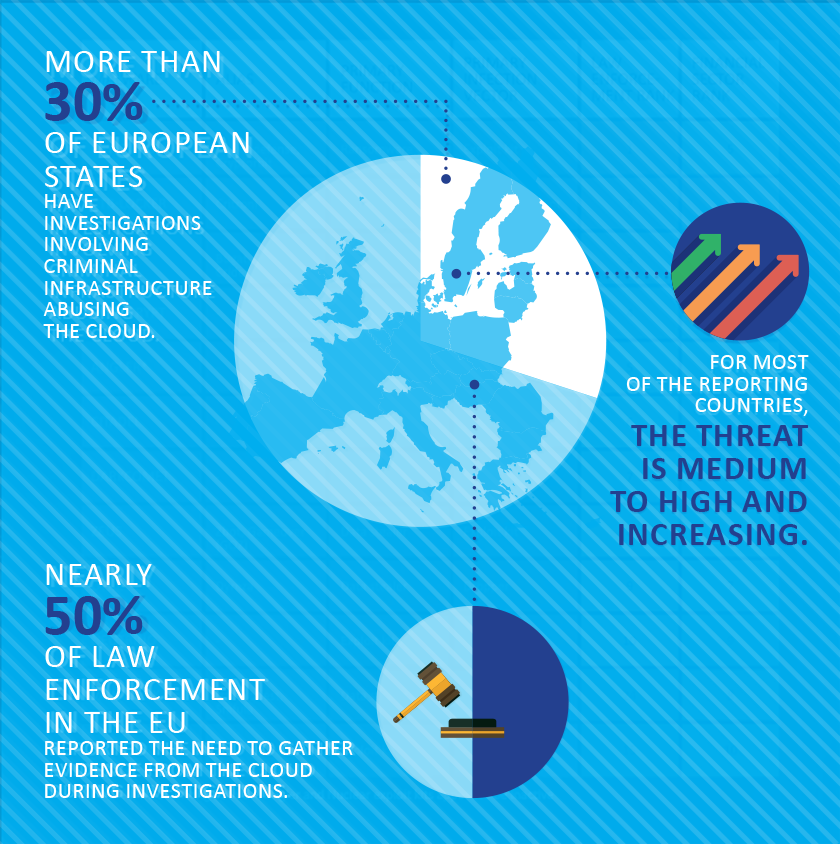
Cloud computing and services provide the environment needed to support the storage and distributed processing of the data collected via the IoT. This links it to the concept of Big Data, which in essence is about new ways of analysing, visualising and leveraging large amounts of data in real-time or near real-time.
These concepts are a driving factor behind new types of ‘critical infrastructure’ such as smart cars, smart ships174 or smart cities. However, they also play a crucial role in more conventional types of critical infrastructure, as more and more smart and connected sensors are being used in such settings too.
For law enforcement, Big Data, the IoT and the Cloud are no longer emerging threats but feature regularly in investigations. While there has been some improvement in terms of law enforcement’s ability in dealing with these threats, the dominating view is that police are still playing catch up in these areas.
As more and more relevant data will be located in the Cloud, cross-border cooperation to access electronic evidence and legal assistance will become even more critical. Consequently, some of the key concerns raised by law enforcement were around the perceived inadequacies of the MLAT process, difficulties in international cooperation and technical and procedural difficulties in seizing evidence stored abroad.